Shield your critical devices and data with Escudo Digital™.
In a world where digital threats evolve every second, protecting government devices and public organizations is no longer optional: it is urgent.
Escudo Digital™ is the threat and anomaly detection system that turns every computer and mobile device into an active barrier against cyber attacks. Installed directly on endpoints, it allows cybersecurity policies to be implemented in minutes, without the need for a complex infrastructure.
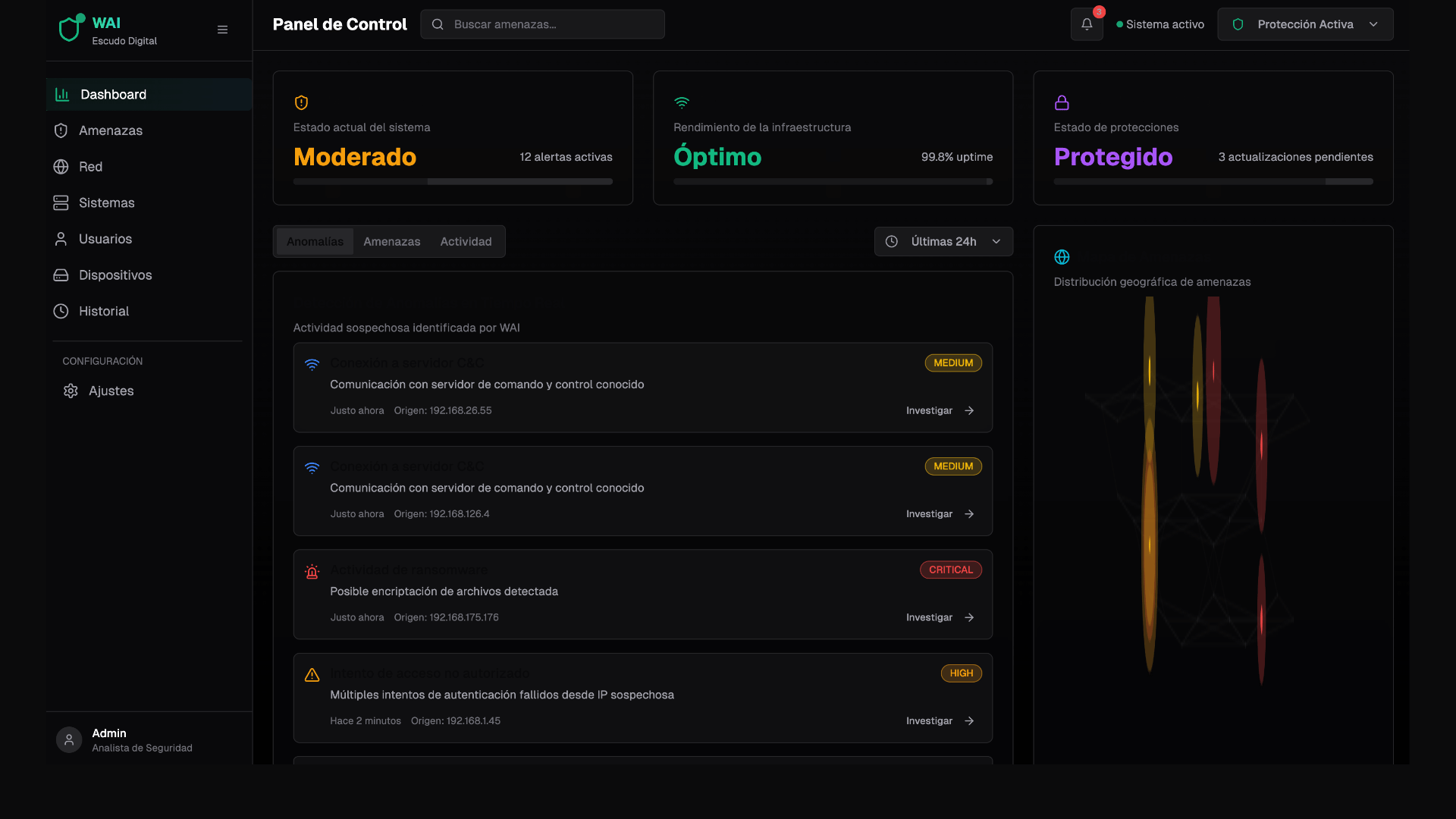
How does it work?

Detects any anomaly
Any suspicious behavior is identified within seconds.

Reacts without asking
In the event of ransomware, it automatically disconnects the computer from the network.

Isolates the threat
If there is a risk, the device shuts down immediately.

Blocks unauthorized remote access
Cut dangerous connections in real time.

Think for you in seconds
AI analyzes device behavior 24x7 and suggests preventive actions.

Managed or unmanaged
You operate it or our Cybersecurity Unit does it.
Actual use cases
Real-Time Ransomware Detection
Identifies massive file encryption patterns before the damage is irreversible. Acts automatically by isolating the computer.
Behavioral Analysis with AI
Detects after-hours connections, anomalous file movements or suspicious installations. No need to wait for a report: take action.
Automatic Incident Response
Disconnects, shuts down or locks an infected device without human intervention. Protects the entire environment before the threat spreads.
Vulnerability Management
Detects and alerts on every known vulnerability (CVE) reported by the National Institute of Standards and Technology (NIST) of the United States, recommending priority patching and updating actions.
Multiplatform Protection
Windows, Linux, Mac, Android, iOS. You protect everything, regardless of device or location.
Compliance and clear policies
Implement homogeneous policies for all devices from a single panel. Everything is traced and audited.
It is not an option. It's now or it's too late.
- More than 70% of cyberattacks target unprotected endpoints.
- A ransomware can encrypt your files in less than 3 minutes.
- An after-hours connection can be the start of a major intrusion.
- Every minute without detection means loss of data, reputation and resources.
Don't wait for the first incident to act.
Our Escudo Digital™ puts cybersecurity within reach of any government.. Protect endpoints. Detect threats. Respond in real time.
Request a demo and learn more about our Digital Shield™. can armor your organization's digital infrastructure.

Company information
News and Events
Popular links
Copyright © 2025. Wai™ is a registered trademark of Wai Technologies SA.







